Scams have not only evolved but have also become increasingly sophisticated. Once limited to phone calls or mail fraud, con artists have turned this into a very lucrative business. The rise of social media, email, and mobile technology has provided scammers with a vast pool of potential targets, allowing them to cast wider nets and reach victims across borders and continents.
Recently, Morrows has observed a surge in scammers following the Medibank Private, Latitude Financial and Optus data leaks. These scammers have specifically targeted individuals whose data and identities were compromised.
Recognising the importance of the situation, we have prepared a series of articles to help you and your clients stay safe. In this article we explain impersonation scams.
What is an impersonation scam?
One of the most common scams these days is an impersonation scam is when a scammer contacts someone by phone or SMS and impersonates a friend, loved one, bank or other service company. Through cunning tactics, they manipulate customers into authorising transactions, making payments, or divulging personal information.
- Random impersonation: Scammers can impersonate by sending a text message (such as Hi Mum) saying they have lost their phone, requesting that they need money urgently to replace a phone or pay an urgent bill, without necessarily researching who they are targeting.
- Sophisticated impersonation: More recently, sophisticated scammers have been going to great lengths to look authentic. Before contacting someone, scammers may do their research and have well-thought-out details at hand, such as partial card and account numbers. This level of detail allows the scammer to gain the customer’s trust as they sound more convincing. Scammers now set up call centres using sophisticated scripts and strategies to come across as more believable and professional. For example, scammers may introduce themselves as an employee from a legitimate using real names and job titles from LinkedIn to try and convince the customer that they’re talking to an authorised employee.
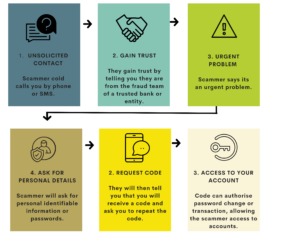
How does a typical Impersonation Scam work?
Below is a chart to explain the typical process the scammers use to gain trust and access to your finances and data.
How Morrows will help protect you and your data
To help safeguard our clients, our team will be following strict processes and protocols:
Our policies are that we:
- Never share sensitive information, such as your tax file number, over the phone or via email without verifying that it is you.
- Always check contact information using a trusted source. If we receive a call requesting sensitive information, we will hang up and call you on a trusted number from our database.
- Continue to store and share sensitive data using a secure online filing system called Box. If you are not using Box or are unsure how to set it up and use it, please reach out to your advisor.
- Continue to monitor and update you on strategies to help keep you safe. Here are two additional articles with tips and advice on keeping your data secure and what to do if you have been compromised or exposed in a data breach.